The video walks you through configuration of 3rd party Network Access Device (NAD) on Cisco ISE 2.0. We will make Aruba IAP work with Cisco ISE on two types of authentication methods: MAB and basic 802.1X. We will review configuration on the Aruba AP required to make it compatible with ISE. Cisco is happy to announce their Fall release, FTD 6.7/ASA 9.15.1/FXOS 2.9, which consists of 104 features across 24 initiatives, addressing technical debt while staying true to our five core investment areas: Ease of Use and Deployment, Unified Policy an. When Cisco ISE is configured for chaining and AC for single mode then AC response with IdentityType TLV to ISE. However, the second identity authentication fails. You can see from this conversation that client is suitable to perform chaining but currently is configured for single mode. WirelessMABCisco (Condition: WirelessMAB AND DeviceType EQUALS Cisco) In the above case, my Authorization Rules would look a lot simpler. Not to mention that if Policy Sets are badly designed, then you're just taxing the CPU and making your logs look more complex than they need to. Lastly, Cisco ISE uses a simple check-box within the allowed-protocols configuration as another method to permit or deny the access into the endpoint database for the MAB request, as seen in Figure-5.
This is a Cisco ISE blog post series with some how-to’s for configuring the ISE deployment, This blog post series exists of 10 parts.
The blogpost Agenda:
Part 1: introduction
Part 2: installation
Part 3: Active Directory
Part 4: High Availability
Part 5: Configuring wired network devices
Part 6: Policy enforcement and MAB
Part 7: Configuring wireless network devices
Part 8: Inline posture and VPN
Part 9: Guest and web authentication
Part 10: Profiling and posture
This week, part 5: Configuring wired network devices
First some terminology and guidelines:
Single host mode / Multi host mode. This defines 1 or multiple hosts on the switchport. Only the first device needs authentication.
Ports are authenticated first before any other traffic can pass.
802.1x is disabled in a SPAN port configuration, trunk ports, dynamic ports, dynamic access ports and etherchannels.
The windows client configuration can be pushed by a GPO. Configuration of this GPO is out of scope for this blog.
Configuration
First, add the RADIUS clients in the ISE deployment.
Click: Administration – Network Resources – Network Devices and click Add. Enter the requested information:
Repeat this step for all devices with ports which need authentication. Don’t forget the Cisco WLC’s if you want to authenticate on wireless.
Click Administration – Network Resources – Network Device Groups – Expand Groups – All Locations and click Add.
Create a location, like “corporate_office” or “hq” and click Submit.
Next, select All Device Types and click Add. In the Name field type Router (or switch, or any other type of device you’re using)
You can create sub layers by type. Like: Routers – 800 or Routers – 2900.
Associate a radius client to a location and device type.
Click – Administration – Network Resources – Network Devices and edit a Radius client. Select the correct Location and Device Type.
Devices (NADs) need TCP 1812 and TCP 1645 for radius communiction to the Policy node.
Configure a router for using radius:
Configure a switch:
In the ISE console you can see the user denied logging. Click Operations – Authenications.
Enabling authentication on clients
First, make sure the correct protocols are selected. Click Policy – Policy elements – Results – Authentication – Allowed protocol – default network access (or create a new one).
In my case, I’ll only enable PEAP and disable all the others.
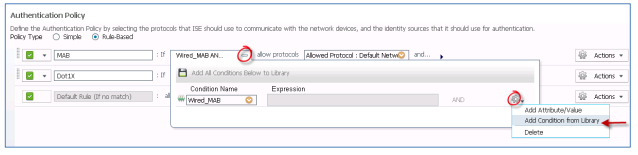
Make sure the correct sequence is used. Click Policy – Authentication. Click the Dot1x rule and change the sequence to AD_then_Local (or the one you desire and created before)
Make sure your switchports are configured as described:
More about ttis configuration in part 6 of this blog post series.
For periodic reauthentication of the switchports every 7200 sec (3600 is default), configure:
Configuring the Win7 Supplicant
Start the “Wired Autoconfig” service in services.msc
Click to your adapter settings and click the tab “authentication”.
Check “enable IEEE802.1x authentication”. For the EAP type, select PEAP in the drop down list.
Click Settings, ensure that Validate Server Certificate is checked. Also make sure that the client does have the root certificate of your CA. Select this root certificate.
Ensure that EAP-MSCHAPv2 is selected and Enable Fast Reconnect is checked.
Check the switchport authentication:
And:
You can check the authentication logging in ISE:
Click Operations – Authentications
Authorization with DACL
Let’s create a DACL that will override the interface port based ACL.
Click: Policy – Policy Elements – Results – Authorization – Downloadable ACLs.
Click Add to create a new one and enter the required ACL:
Click Policy – Policy Elements – Results – Authorization – Authorization Profiles. Click Add, give this profile a name and select the DACL in the drop down menu. Check the reauthentication checkbox!
Make sure there is an Active Directory group available with the needed computer accounts. Make this group available in ISE:
Click Adminsitration – Identity management – External identity – Sources – Active directory – groups.
Click Add – select groups from directory and add the group.
Now it’s time to create a authorization policy. Click Policy – Authorization, click the down arrow at a rule, click Insert new rule above.
Click Create new condition (Advanced option)
Fill in the Expression and correct user group.
In the ‘then’ portion of the rule, add a authorization policy. Click the created Dot1x authorization policy.
That’s it, start testing!
Next week part 6 of this blog post series: Policy enforcement and MAB
Cisco Identity Services Engine (ISE) may be used for guest management when paired with Meraki Access Points. Cisco ISE is another option for authorizing users, enabling many additional business use cases.
Meraki APs will pass necessary information over to Cisco ISE using MAC-based authentication and honor a Uniform Resource Locator (URL) redirect that is received from the Cisco ISE Server. Using change of authorization (CoA), the Cisco ISE server can ensure that the correct authorization is applied to the end user devices based on the authentication status.
Expected Packet Flow
Cisco Ise Mab Config
Client machine associates to the web authentication SSID
Client MAC address is sent to RADIUS server as a username and password (Access-Request) by MR, and the MR responds to the client machine acknowledging the association request
ISE server responds with an RADIUS Access-Accept and a redirect URL
Client machine gets an IP address and DNS server address through DHCP
Client machine tries to reach a webpage which results in an HTTP GET packet
MR intercepts the GET packet and sends redirect URL instead (with webpage hosted on ISE)
Client machine authenticates on the ISE web portal
- RADIUS server then sends a CoA request (CoA requests work on UDP Port 1700) with a request to re-authenticate, also indicating that user is valid
- MR sends CoA-ACK
- MR Authenticator sends an Access-Request with existing client machine's session-ID and MAC address
ISE server then responds back with Access-Acccept and any extra ISE functions after client's successful authentication to web portal
Client is allowed access to the network
Configuration
The following sections of this guide will outline a configuration example with using Cisco ISE as the guest management system which is also hosting the captive portal.
Meraki Access Point Dashboard Configuration
The Meraki Access Point configuration is outlined below all on the Access Control Page for a particular SSID (Wireless > Configure > Access Control).
Configure MAC-Based Authentication
Select MAC-based access control from the association requirements section of the access control page.
Enter the details for the RADIUS server including the IP address, port, and secret. If using Group Policies select Airspace-ACL-Name for the RADIUS attribute specifying the group policy name. The Airspace-ACL-Name must match the name of one of your group policies configured under Network-wide > Group Policies. Enable CoA support if there is a requirement to change the attributes of an authentication, authorization, and accounting (AAA) session. Hack game drag racing 4x4.
Configure CWA for Splash page
SelectCisco Identity Services Engine (ISE) Authentication in the Splash Page section of the access control page. This setting will honor the Cisco custom url-redirect attribute sent from Cisco ISE.
Configure the Walled Garden
The IP address of the Cisco ISE server needs to be added to the walled garden to ensure that a client will be permitted through the walled garden before being authenticated by the Cisco ISE server.
DNS traffic is permitted by default through the walled garden
Disable CNA
As of Cisco ISE 2.2, Apple CNA is supported for Guest and BYOD. Beginning July 26th, 2017, Apple CNA and Android captive portal detection are enabled by default on Cisco Meraki MR access points. On iOS 7+ and OS X, the client will automatically launch a mini-browser (CNA) that takes the user to the splash page to complete authentication and gain access to the network. Android devices will display a notification on the device prompting the user to sign into the Wi-Fi network. Tapping the notification will launch the device browser and direct the user to the splash page. To disable CNA and captive portal detection, append the following 17.0.0.0/8 IP rangeand domain names to the walled garden as shown below:
Disabling CNA will require that users manually open their web browser before being presented with the splash page. Applications on the user's device that require Internet connectivity will not function as expected until the user has opened their web browser and completed authentication via the splash page.
Cisco ISE Configuration
The following sections focuses on Cisco ISE 2.4 and it will present a basic configuration with default web portal from Cisco ISE. For more information about web portal customization please look into ISE documentation.
Adding Managed Network Devices
MR access points acting as authenticators (devices through which AAA requests are sent to Cisco ISE) need to be added to ISE before Access-Request will be answered, it will by default not answer any requests.
To add a new device:
In Cisco ISE, choose Administration > Network Resources > Network Devices.
From the Network Devices navigation pane on the left, click Network Devices.

Click Add, from the action icon on the Network Devices navigation pane or click an already added device name from the list to edit it.
In the right pane, enter the Name and IP Address. As for the mask, you can add devices inside a network using /24, or as needed to avoid manually importing several APs.
Check the Authentication Settings check box and define a Shared Secret for RADIUS authentication. This must match the Secret entered for the RADIUS server when configuring the SSID in Dashboard.
- Click Submit
Once a device is added, it will show up on the device list in ISE.
Creating Results for Rules
A new results needs to be created where the redirection will be specified.
To do this, go to “Policy > Results”. Click on Authorization and Authorization Profiles.
Click on “Add”
Name this authorization profile.
On Common Tasks, select “Web Redirection (CWA, MDM, NSP, CPP)”, choose Centralized Web Auth, on ACL “NULL” and Value “Self-Registered” (These values can change depending on your needs.
Optionally, Static IP can be used to not used a DNS server, however, this is not recommended because the IP of the ISE server will be clear text and visible for the end client.
Enabling Policy Sets
Cisco ISE supports policy sets, which allow grouping sets of authentication and authorization policies, as opposed to the basic authentication and authorization policy model, which is a flat list of authentication and authorization rules. Policy sets allow for logically defining an organization's IT business use cases into policy groups or services, such as VPN and 802.1X. This makes configuration, deployment, and troubleshooting much easier.
In Cisco ISE, choose Administration > System > Settings > Policy Sets.
Cisco Ise Wired Mab Configuration
Creating a Policy Set
Click on Policy > Policy Set
Click the plus (+) sign or click on the settings icon and Create above to create a new policy set.
Enter the Name, Description and a Condition for this group policy.
Click on Condition, a new menu will show, match the condition necessary, per SSID policy sets are recommended, therefore, attribute “Radius·Called-Station-ID” ENDS WITH “<SSID name>” is the preferred option. Click “Use” after configuring this step.
Define allow protocols, by default “Default Network Access” can be used.
Click on “Save”
Create Authentication Policy
Click on “View” policy by clicking on the right arrow.
Click on ”Options”
Change “If user not found” to CONTINUE
Create Authorization Policy.
Two rules are required in Authorization Policies for Central Web-Auth, one rule will prompt the redirection and the second rule will grant access once the client machine has passed web page authentication.
Click on Authorization Policy
Click on the (+) sign or on the settings Icon to create a new rule.
Click on “Condition”. a new window will pop up. In this window, the method of the client requesting access can be selected.
Look for Called-Station-ID, and match it to the name of the SSID.
Click “Use”
Select on “Results”, the name of the profile created for redirection, in this case it is “CWA”.
For second rule click on the Action Icon and select “Insert new row above”
Click on “Condition” a new window will pop up, in this window the method of the client requesting access can be selected.
Look for “IdentityGroup:Name”
- Select “In” and “Endpoint Identity Groups: GuestEndpoints”.
Click on “Use”.
Select on “Results” the profile called “PermitAccess”
Click Save.
Both rules should be created and should look like the image below, order is very important.